Data Security Assessment
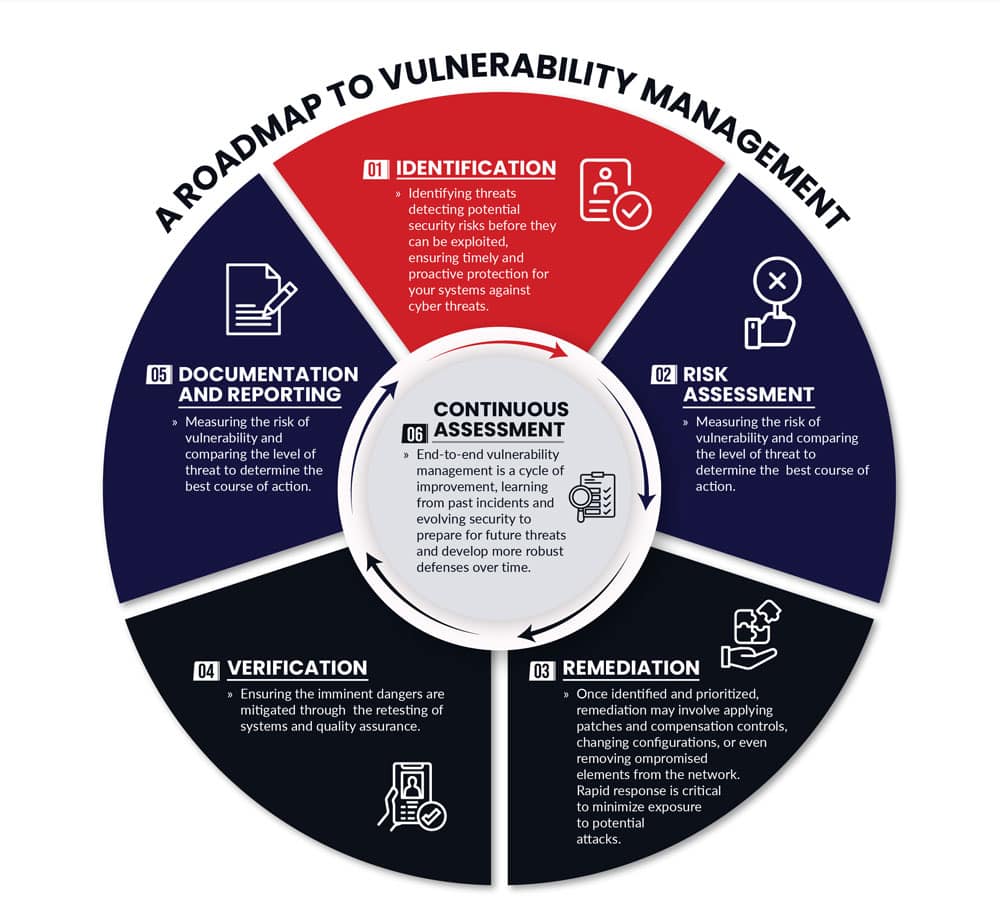
We work with your IT team to analyze the state of current vulnerability management efforts and identify all contributing factors to vulnerability issues across people, processes, and technology areas. This provides a comprehensive look at how to enhance your existing security policies and what gaps may need to be filled. These reviews evaluate:
- Data governance and architecture documents, data security standards and controls, corporate security policies and procedures, and data asset inventories
- Data security measures, such as discovery and loss prevention tools, encryption and key management, and application, system, and user access management controls