The iCloud Security Breach: Did We Learn Anything?
There was yet another security breach at a major company recently, and it seems this is becoming an all too familiar headline. This time the breach affected one of the most recognized brands in the world, Apple Inc., as well as a number of well-known celebrities. The breach not only raised concerns about security but also privacy. If you’re wondering what that sound in the distance is…it’s most certainly a broken record. Could we be doing more to better secure the cloud? Has Apple taken action since this major breach? Here we discuss what the breach means to the common user and what Apple has done to ensure it doesn’t happen again.
In case you didn’t hear or see any of the wall-to-wall coverage several weeks ago a number of well-recognized celebrities were “hacked” and their nude photos were stolen and released to the public. It is believed that there was a security breach of the iCloud service (which Apple has denied) and that the security lapse compromised the privacy of users. Of course, your first thought is probably, “Why would you have nude photos of yourself in the cloud?”. This is an incisive question indeed. The reality is a lot of our private information including pictures, documents, and more now live in the cloud. As of last year iCloud was the most used cloud storage service in the United States beating out other major players such as Dropbox and Amazon by an almost 2-1 margin. We are storing less and less on our personal machines and more and more on cloud servers we can essentially access from anywhere. This also makes it easier for hackers or cyber-thieves to access your data if it’s not properly secured.
Now, whether it really was Apple’s fault, or whether the affected celebrities had lax passwords, or it was Dade, Kate, Joey, or Cereal (10 points for the movie reference) certainly matters. However, what’s done is done, and the important part is learning from these incidents to make sure they don’t happen again. It appears as if Apple, despite its denial of wrongdoing, is taking measures to tighten security.
Apple has increased its use of the “two step verification” process that helps to protect user’s data (shown below). The process works by requiring an additional step after a person enters their username and password information on a device they have not used before. They are required to enter a four digit “verification code” that is sent to a trusted mobile phone number or via Apple’s Find My iPhone app. If the code is entered incorrectly, or not at all, that person or device is denied access to iCloud and are blocked from making iTunes or App Store purchases. The account can only be recovered using a 14-digit recovery code. The two step verification is an opt-in service, however, and not yet a requirement despite the suggestion of many pundits.
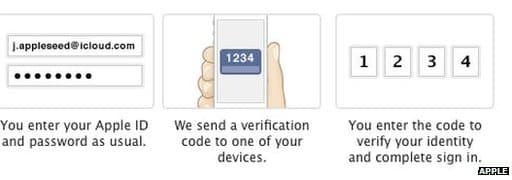
While Apple had implemented the two-step verification in the past, it was only featured when using the backup service and did not adequately protect the actual backed up data and was more a function to stop cyber-thieves from stealing or guessing passwords. This feature also did not block access from software such as Elcomsoft’s Phone Password Breaker; software used by many law enforcement agencies to gain access to a suspect’s iPhone or iPad. The creator of the software suggested his product was likely used in the attack on the celebrity accounts, however, that Apple’s recent changes guard against the technique that was used. Finally, adding another level of comfort for users is the ability for account owners to receive an email anytime a backup begins downloading, regardless of whether the two step authentication is turned on.
While Apple has stated it will take firm action to further recommend that users switch to two-step authentication it is not yet a default feature. Many experts, and users for that matter, believe the current one step authentication process is not secure enough and that two-step should become the norm. Whether this is something that will happen or not remains to be seen, but for the foreseeable future it seems we will have to “opt-in” for advanced security measures.
If the recent security breaches have taught us anything, it’s that security can be better. Cyber-thieves are constantly looking for new ways to break down security barriers, and companies and cloud providers should be consistently driving for better security measures. In the meantime, users should be mindful of what they put in the cloud and take their own security precautions as much as possible. If we all work together and are more diligent, the more secure our data will become.